QuickSight Interactions with IAM Policies
Introduction
We were tasked with understanding how IAM policies interact with QuickSight
QuickSight Terms
- Data Source - S3 bucket, Athena, uploaded CSV file etc.
- Dataset - Data Added to QuickSight from a Data source.
- Analyses - Where the data is put into reports
- Dashboard - A published analysis
QuickSight Actions
Admin-user accessed QuickSight via the console and thus became an admin user. They invited Test-user to access QuickSight originally as a Reader. what did we do around groups etc
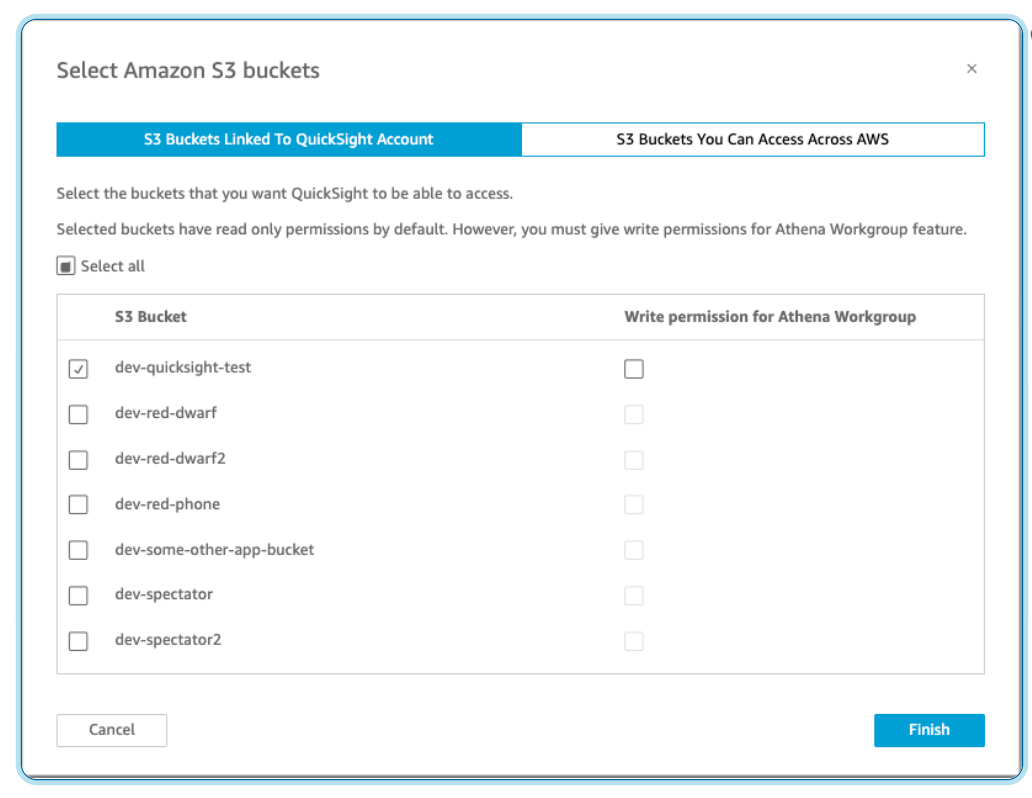
As the Admin-user, the test S3 bucket dev-quicksight-test was was added to the list of S3 buckets available via QuckSight Access to AWS services, under “Security & permissions”.
The Admin-user created a new QuickSight user group to which Test-user’s account was added and IAM policies granted to this group. Going forward it may be best to think of this as a per application where collaborating authors could be added whom required access to the data source.
QuickSight Sharing Actions
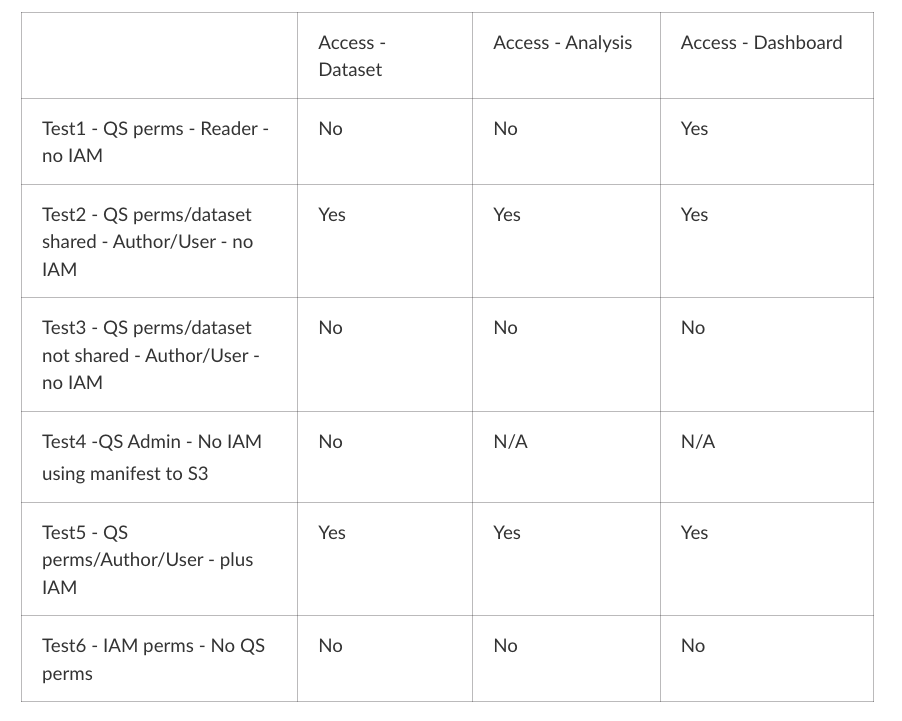
Using Test-user’s account with increasing levels of access.
- Test1 - Account had the minimum level of Access, that of reader with no IAM access granted.
- Test2 - Account set to Author, owner grants shared access to Dataset/Analysis/Dashboard with no IAM access granted.
- Test3 - Account set to Author, no access granted by owner to Dataset/Analysis/Dashboard with no IAM access granted.
- Test4 - Account set to Admin, attempt to access data source (S3) directly using manifest file with no IAM access granted.
- Test5 - Account set to Author, member of QuickSight user group, attempt to access data source (S3) directly using manifest file with IAM access granted.
- Test6 - Account set to Author, not a member of QuickSight user group, attempt to access data source (S3) directly using manifest file with IAM access granted.
QuickSight Athena Actions
- Created a new policy for S3 access
poc-quicksight-user-access(see Annex A) granting access to BucketA - Created new QuickSight group called user_access
- Removed Test-user’s user from the QuickSight admin group and added to user_access group
- Tested S3 bucket access using this policy and Test-user was able to access one S3 BucketA but not BucketB
- Added BucketB into the policy
poc-quicksight-user-accessand then could access BucketB via QuickSight - Created new policy for Athena access
poc-quicksight-user-access-athena(see Annex A) assigned to the user access group. So user user_access group has two policies assignedpoc-quicksight-user-access&poc-quicksight-user-access-athena. - Test-user could create datasets via Athena for both databases/S3
- Removed access from the S3 policy
poc-quicksight-user-accessfor the BucketB bucket. - Tried to create a dataset via Athena Test-user could still see both Databases* but was unable to retrieve data from the database where access had been removed to the S3.
* QuickSight has access to list Athena databases using the IAM policy poc-quicksight-user-access-athena which will allow users to see multiple databases/tables to which they may not have access, BUT they will only be able to retrieve data from databases/tables to which they have been granted access via the IAM policy poc-quicksight-user-access.
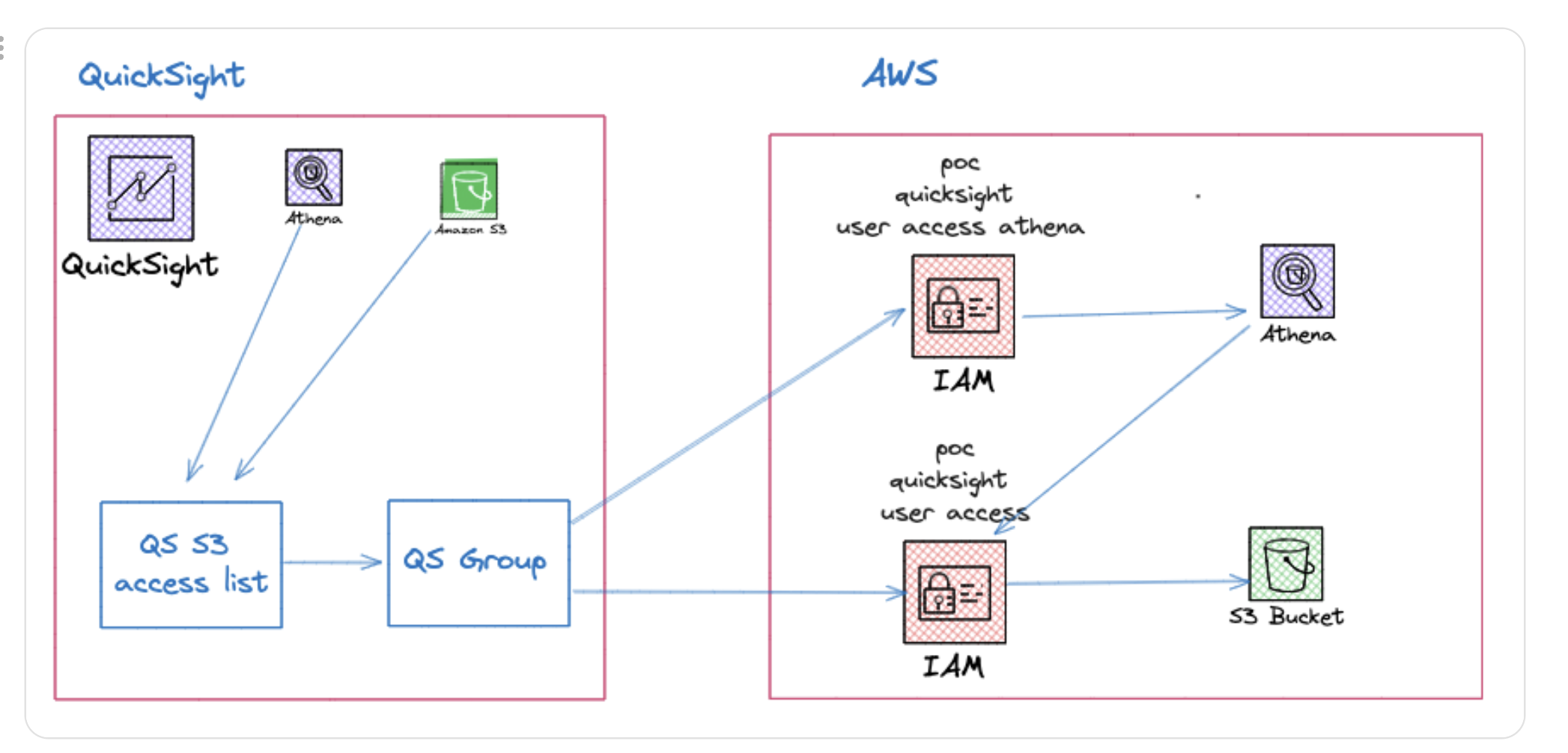
QuickSight Access Flow
- QuickSight must have any S3 bucket to which access is required added to the QuickSight S3 access list.
- A IAM policy for access to the S3 Bucket must be created in AWS
- Within QuickSight individual users or user group be granted access to the IAM policy
- In addition if Athena access is required a IAM policy to list databases/tables must be created in AWS and granted to the QuickSight group. This is generic and not specific to individual databases and does NOT grant access to any data.
Test User Account Deletion
Prior to deleting Test-user’s email user account, they shared the following dashboards, analyses and datasets with my account (admin). They shared one of each resource with my user as a co-owner, and additionally as a viewer for a dashboard and dataset.
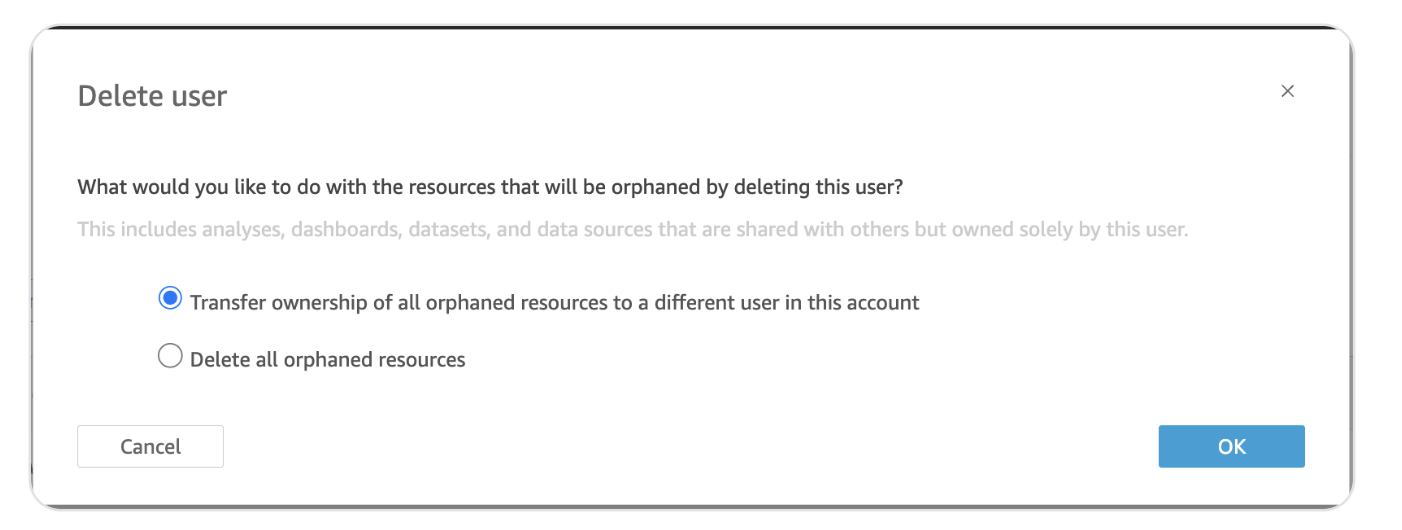
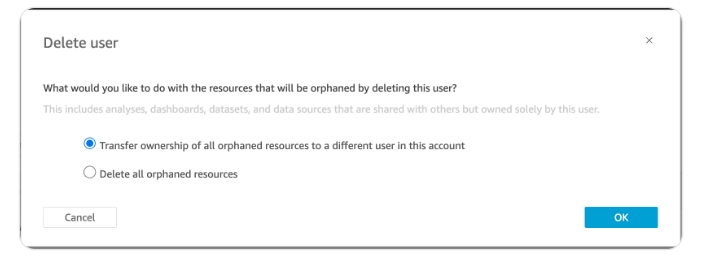
When deleting Test-user’s account, the below options were provided. The option to delete orphaned resources was selected.
When deleting Test-user’s account, the below options were provided. The option to delete orphaned resources was selected.
After deleting the Test-user’s account, I still had the ability to access the resources shared with my user. For the resources I was shared as a viewer, this means I wouldn’t be able to edit these resources and they would no longer maintainable follow the user deletion.
In the event that an account was to be deleted from QuickSight, the first option to transfer ownership for orphaned resources should be used, except in the scenario that all resources have already been co-owned with another user.
Conclusions/Findings
Scenarios
User has IAM permission but not QuickSight permissions, can they see data in a shared dataset
- A data set is data pulled into QuickSight by a user that has access to the data source in S3
- This can then be shared with a QuickSight User that has Author access - they do not need any QuickSight or IAM permissions
User has QuickSight permissions but not IAM permissions, can they see data in a shared dataset
- Again any author can have a data set shared with them regardless of the users QuickSight/IAM permissions
Users have IAM permissions but not QuickSight can they create data sources
- No - to access a data source, an S3 bucket for example, the bucket must be in the QuickSight S3 access list, an appropriate IAM policy with access to the bucket must granted to the user/group and only if both are in place can a data source be accessed.
Findings
- A user with access to a data source can create a QuickSight dataset and share that with any QuickSight Author regardless of that users access to the data source, thus bypassing any current application access control.
- QuickSight groups can contain multiple users
- Database access is restricted by the S3 policy not the Athena policy.
- Each application/team would need its own QuickSight group and an IAM S3 policy granting access to one or many S3 buckets.
- Any access to S3 is by having access granted in both QuickSight group and IAM policy
- A dataset can be shared by the owner within QuickSight with another user who does not have IAM access to the data source.
- A data source owner cannot share a data source only a dataset within QuickSight
Annex A - IAM policies created for this test.
poc-quicksight-user-access
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "GetObjects",
"Effect": "Allow",
"Action": [
"s3:GetObjectVersion",
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::dev-quicksight-test",
"arn:aws:s3:::dev-quicksight-test/"
]
},
{
"Sid": "ListBucket",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": [
"arn:aws:s3:::dev-quicksight-test",
"arn:aws:s3:::dev-quicksight-test/"
]
}
]
}
poc-quicksight-user-access-athena
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":[
"athena:BatchGetQueryExecution",
"athena:CancelQueryExecution",
"athena:GetCatalogs",
"athena:GetExecutionEngine",
"athena:GetExecutionEngines",
"athena:GetNamespace",
"athena:GetNamespaces",
"athena:GetQueryExecution",
"athena:GetQueryExecutions",
"athena:GetQueryResults",
"athena:GetQueryResultsStream",
"athena:GetTable",
"athena:GetTables",
"athena:ListQueryExecutions",
"athena:RunQuery",
"athena:StartQueryExecution",
"athena:StopQueryExecution",
"athena:ListWorkGroups",
"athena:ListEngineVersions",
"athena:GetWorkGroup",
"athena:GetDataCatalog",
"athena:GetDatabase",
"athena:GetTableMetadata",
"athena:ListDataCatalogs",
"athena:ListDatabases",
"athena:ListTableMetadata"
],
"Resource":[
"*"
]
},
{
"Effect":"Allow",
"Action":[
"glue:GetDatabase",
"glue:GetDatabases",
"glue:GetTable",
"glue:GetTables",
"glue:GetPartition",
"glue:GetPartitions",
"glue:BatchGetPartition"
],
"Resource":[
"*"
]
},
{
"Effect":"Allow",
"Action":[
"s3:GetBucketLocation",
"s3:GetObject",
"s3:ListBucket",
"s3:ListBucketMultipartUploads",
"s3:ListMultipartUploadParts",
"s3:AbortMultipartUpload",
"s3:CreateBucket",
"s3:PutObject",
"s3:PutBucketPublicAccessBlock"
],
"Resource":[
"arn:aws:s3:::aws-athena-query-results-*"
]
}
]
}
Deny policy tested:
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"denyS3",
"Effect":"Deny",
"Action":"s3:*",
"Resource":"*"
}
]
}